Exploring DeepSeek R1
Analyzing DeepSeek R1's strengths and weaknesses while comparing it to larger closed-source models using the same prompt.

DeepSeek has made waves in the AI community with its latest release, DeepSeek R1, a reasoning-focused model that builds upon the foundation of DeepSeek V3. Unlike its predecessor, this model emphasizes structured reasoning and problem-solving rather than raw text generation. DeepSeek R1 is MIT-licensed, fully open-source, and allows unrestricted commercial and research use. This is a big deal! Access to a high-quality, open-source reasoning model means increased transparency, the ability to fine-tune models for security applications, and the potential for integrating advanced reasoning into cybersecurity automation tools.
This review will discuss the model’s strengths, weaknesses, and real-world implications for security research and development. I'll also provide hands-on test cases highlighting where DeepSeek R1 shines and still falls short.
Benchmarks: Performance and Capabilities
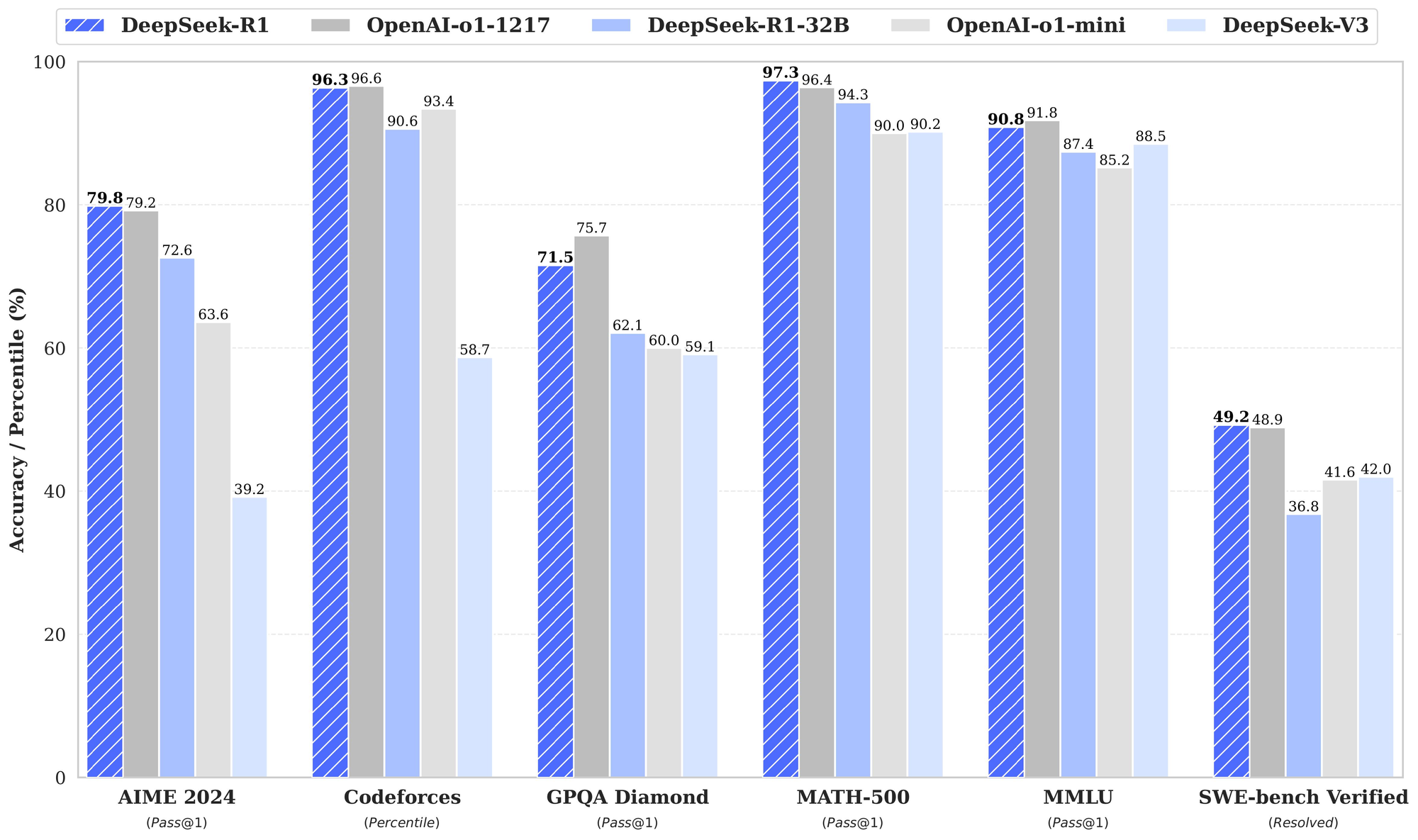
Benchmark results place DeepSeek R1 in direct competition with proprietary models like GPT-4o and Claude 3.5 Sonnet in reasoning tasks. In key evaluation areas like GSM8K (math problem-solving), MMLU (general knowledge), and ARC (advanced reasoning), DeepSeek R1 performs exceptionally well, often surpassing OpenAI's 01-mini model.
Key Observations
- Mathematical Reasoning: It demonstrates near-state-of-the-art accuracy, outperforming many proprietary models.
- Logical Deduction: Excels at multi-step reasoning but sometimes overthinks simple tasks.
- Memory & Context Awareness: Handles complex prompts well but lacks some memory, as seen in non-reasoning models such as GPT-4o.
- Code Generation: Probably its strongest suit. In testing, I noticed it can reason through algorithmic logic often better than o1 can.
- Security Implications: Lacks structured output support (e.g., JSON), making it less ideal for automation workflows requiring function calling or structured responses.
Architecture and Approach to Reasoning
DeepSeek R1 is a Mixture of Experts (MoE) model, similar to DeepSeek V3. It consists of 671 billion total parameters, but only 37 billion are active at any given time. This dynamic expert selection allows the model to be efficient while leveraging specialized knowledge areas dynamically.
One of the defining features of DeepSeek R1 is its self-reasoning approach. Instead of relying solely on supervised fine-tuning, the model is trained with a unique RL-based self-dialogue mechanism. This means that R1:
- Thinks before answering, often breaking problems down into structured reasoning steps.
- Evaluates its own responses, refining its approach mid-generation.
- Uses a
<think></think>tag system to simulate human-like inner dialogue.
This makes it highly reliable for logical tasks but also introduces verbosity issues. Sometimes, R1 generates excessive thought processes before arriving at an answer.
('a_c', 'Alert Code'),
('a_n', 'Alert Name'),
('a_t', 'Alert Type'),
('d_co', 'Destination Country Code'),
('d_la', 'Destination Latitude'),
('d_lo', 'Destination Longitude'),
('d_s', 'Destination State/Region'),
('s_co', 'Source Country Code'),
To format the long names into a CSV header, you can extract the second element from each tuple and join them with commas. Here’s how the CSV header would look:
Alert Code,Alert Name,Alert Type,Destination Country Code,Destination Latitude,Des
Alright, so I've got this query where the user provided a list of tuples. Each tuple has two elements: a short code and a corresponding long name. The last one is a bit different because it's (None, 'Timestamp'). They want me to format these long names into a CSV header.
Hmm, first I should understand what exactly they're asking for. It looks like each tuple represents a column in a dataset, where the first element is either an abbreviated code or None, and the second is the full name of that column. The user wants these full names as headers in a CSV file.
So, my task is to extract all the long names from the tuples and arrange them in a single line separated by commas. That way, they can be used directly as the header row in a CSV file.
Looking at the list:
- ('a_c', 'Alert Code')
- ('a_n', 'Alert Name')
- ('a_t', 'Alert Type')
- ('d_co', 'Destination Country Code')
- ('d_la', 'Destination Latitude')
- ('d_lo', 'Destination Longitude')
- ('d_s', 'Destination State/Region')
- ('s_co', 'Source Country Code')
- ('s_lo', 'Source Longitude')
- ('s_la', 'Source Latitude')
- ('s_s', 'Source State/Region')
- (None, 'Timestamp')
I need to take the second element from each tuple. That would be 'Alert Code', 'Alert Name', and so on until 'Timestamp'.
Wait a minute, there's a potential issue here. I notice that in the third tuple, it's ('d_lo', 'Destination Longitude'), but longitude usually comes after latitude. But looking at the list, 'Destination Latitude' is before 'Destination Longitude', which makes sense because latitude comes first. Wait no, actually in standard terms, longitude often follows latitude, so maybe the order here is correct.
But perhaps I should double-check the order of the fields to ensure they're in the correct sequence as per the user's data structure. The order given by the user seems intentional, so I'll follow that without changes.
Now, for the last tuple where the first element is None. That probably means it doesn't have a short code, but the long name is 'Timestamp'. So I just include 'Timestamp' in the header as the last column.
Putting them all together, separated by commas, should do it. Let me list them out:
Alert Code, Alert Name, Alert Type, Destination Country Code, Destination Latitude, Destination Longitude, Destination State/Region, Source Country Code, Source Longitude, Source Latitude, Source State/Region, Timestamp
I think that's correct. I just need to make sure there are no typos and the order is preserved as given.
Here’s the formatted CSV header based on the long names:
Alert Code, Alert Name, Alert Type, Destination Country Code, Destination Latitude, Destination Longitude, Destination State/Region, Source Country Code, Source Longitude, Source Latitude,
Where DeepSeek R1 Excels
1. Mathematical and Logical Problem Solving
DeepSeek R1 is one of the most substantial open-source models for complex math reasoning. Unlike traditional LLMs that might rely on pattern recognition, it follows a step-by-step deduction process.
Solve this math problem step by step:
A train leaves City A at 60 mph. Another train leaves City B, 120 miles away, at 40 mph heading towards City A. When do they meet?
First, I need to determine the speeds of both trains and the distance between their starting points.
Train A is traveling at 60 mph from City A, and Train B is traveling at 40 mph from City B, which is 120 miles away.
Since both trains are moving towards each other, their relative speed is the sum of their individual speeds. So, I add 60 mph and 40 mph to get a combined speed of 100 mph.
Next, I use the formula for time, which is distance divided by speed. The distance between City A and City B is 120 miles, and the combined speed is 100 mph.
By dividing 120 miles by 100 mph, I find that it will take 1.2 hours for the two trains to meet.
Sure, let's solve the problem step by step.
Problem Statement: A train leaves City A at 60 mph. Another train leaves City B, which is 120 miles away, at 40 mph heading towards City A. When do they meet?
Step-by-Step Solution:
2. Multi-Step Deductive Reasoning
DeepSeek R1’s internal thought process efficiently breaks down multi-step logic problems.
Alice, Bob, and Charlie are standing in a row. Alice sees Bob and Charlie, Bob sees Charlie, but Charlie sees no one. Each person wears a hat, which can be either red or blue. If Alice sees one red and one blue hat, and Bob sees a blue hat, what colo
Okay, so I've got this puzzle here about Alice, Bob, and Charlie standing in a row. Each of them has a hat that's either red or blue. The problem gives me some information about what each person can see and asks me to figure out the color of Charlie's hat.
Let me try to break it down step by step. First, I should probably visualize their positions. It says they're standing in a row, so let's assume Alice is first, then Bob, and then Charlie at the end. So, from left to right: Alice, Bob, Charlie. That makes sense because if Alice sees both Bob and Charlie, she must be in front of them. Similarly, Bob can see Charlie but not Alice because he's behind her.
Alright, so each person has a hat—either red or blue. Now, the problem states:
- Alice sees one red and one blue hat.
- Bob sees a blue hat.
And we need to figure out what color Charlie's hat is.
Let me write down what each person can see:
Alice can see both Bob and Charlie's hats. So, she has a view of two hats. She notices that one is red and the other is blue.
Bob can only see Charlie's hat because he's behind Alice. He sees that Charlie's hat is blue.
Wait, hold on—is that correct? If Alice is in front, Bob is in the middle, then Charlie is at the end. So actually, Bob would be able to see Charlie but not Alice because she's in front of him. Similarly, Alice can see both Bob and Charlie since they're behind her. So the original assumption holds.
Given that, if Bob sees a blue hat on Charlie, he knows that. Then, why does the problem say "Bob sees a blue hat"? Is it necessarily Charlie's? Or could it be someone else's?
Wait, no—if Alice is in front of Bob, then Bob can only see Charlie because he's behind him. So yes, if Bob says he sees a blue hat, that must mean Charlie's hat is blue.
But hold on—is there more to this? Let me double-check the problem statement: "Alice, Bob, and Charlie are standing in a row. Alice sees Bob and Charlie, Bob sees Charlie, but Charlie sees no one." So it confirms that:
- Alice can see both Bob and Charlie.
- Bob can only see Charlie.
- Charlie cannot see anyone because he's at the end.
So when the problem says "Alice sees one red and one blue hat," she is looking at Bob and Charlie. Since there are two hats, she must see either two different colors or same colors. But in this case, it's specified that Alice sees one red and one blue. So that tells me that between Bob and Charlie, one has a red hat and the other has a blue.
Then, the problem states "Bob sees a blue hat." As established earlier, since Bob can only see Charlie, that must mean Charlie's hat is blue. Therefore, if Alice saw one red and one blue, and we now know Charlie's hat is blue, then Bob must be wearing the red hat.
Wait, but hold on—what color is Charlie's hat? If Bob sees a blue hat on Charlie, and Alice sees one red and one blue, which would mean that either Bob is red and Charlie is blue or vice versa. Since Bob is in front of Charlie, when he looks back, he can only see Charlie.
So if Bob saw a blue hat, meaning Charlie's hat is blue, then from Alice's perspective, she's seeing Bob (who must be wearing the other color) and Charlie (blue). So Bob would have to be red because she sees one red and one blue. Therefore, that means Charlie has a blue hat.
Wait, so I think this is straightforward? If Bob can see Charlie's hat and it's blue, then Alice sees both of them: Bob in front with a red hat and Charlie behind him with a blue hat. So, from Alice's point of view, she sees one red (Bob) and one blue (Charlie). That satisfies the condition.
So is that the answer? Is Charlie's hat blue?
But let me consider another angle—is there any trick here or something I might have missed? Sometimes in logic puzzles, if people are aware of what others can see, they might deduce more information.
Wait a second—if Bob saw that Charlie had a red hat, would that change anything? Let me explore that possibility.
Suppose Charlie's hat were red. Then Bob, seeing Charlie's red hat, would know that. But in this case, Alice sees one red and one blue—Bob and Charlie. So if Charlie is red, then Bob must be blue because Alice saw one of each. If Bob had a blue hat, he'd see Charlie with a red hat. Is there any statement from Bob? The problem says "Bob sees a blue hat." Wait, no—the problem doesn't say that Bob says anything; it just states what he sees.
So in the problem: Alice's observation is that she sees one red and one blue. Bob's observation is that he sees a blue hat (which must belong to Charlie). So from that, we can directly conclude that Charlie's hat is blue without any further deduction needed.
Is there an alternate scenario where Charlie's hat could be something else? Let me see.
Suppose all three have hats, but the problem only tells us about Alice and Bob's observations. There are four possible combinations for Bob and Charlie: both red, both blue, or one of each.
But given that Alice sees one red and one blue, so the pair (Bob, Charlie) must consist of one red and one blue. Then, if Bob sees a blue hat on Charlie, it means that Charlie's hat is blue; therefore, by elimination, Bob must have a red hat.
Therefore, yes, Charlie’s hat is blue.
Wait, but just to make sure I'm not missing any other layers here—it says each person wears a hat which can be either red or blue. So there are three hats: Alice, Bob, and Charlie's. But the observations only give information about two of them—Bob and Charlie—from Alice and Bob’s perspectives.
Is it possible that considering what Alice knows, she could deduce something more? Let me try to think from each person's perspective.
Starting with Alice: She can see both Bob and Charlie's hats. She notices one is red and the other blue. So for her, if she had a red hat, then the two hats behind her (Bob and Charlie) would need to be... wait, no—Alice cannot see her own hat, so when it says "Alice sees one red and one blue," that's only about Bob and Charlie.
So regardless of Alice's own hat color, from her viewpoint, she can tell that between Bob and Charlie, there's a red and a blue. So if she had a red hat on herself, or blue, we don't know, but the problem doesn't specify anything about what Alice does with that information; it just tells us that this is what she sees.
Similarly, Bob only has information about Charlie's hat—it's blue. He can't see his own hat either, so he knows that Charlie's hat is blue. Therefore, from his perspective, when combined with Alice's statement, perhaps more can be deduced?
Wait, but in the problem statement, do we know anything about what the others are thinking or deducing? It just says that each person has a hat; it doesn't specify any communication between them or any deductions made beyond their immediate observations.
Therefore, if we have Alice observing one red and one blue on Bob and Charlie. And Bob seeing a blue hat—on Charlie, so therefore, Charlie's hat is blue.
So then by elimination, Bob must be wearing the red hat since Alice saw one of each color. So yes, that seems solid.
Is there any other angle? Maybe considering that if Bob saw a different color, would he have different information?
Wait, suppose Bob had seen a red hat on Charlie. Then he might not know his own hat color. But in this case, he sees blue, so we can conclude Charlie's is blue.
Therefore, putting it all together: Alice sees one red and one blue—Bob (red) and Charlie (blue). Therefore, Charlie’s hat must be blue.
I don't think there are any other possibilities here because the constraints directly point to that conclusion. So I guess I'm confident in that answer.
Final Answer \boxed{blue}
Alice, Bob, and Charlie are standing in a row from left to right: Alice, Bob, and Charlie. Each person wears a hat that can be either red or blue. The problem states:
- Alice sees one red and one blue hat on Bob and Charlie.
- Bob sees a blue hat
3. Geopolitical and Hypothetical Reasoning
It can reason through complex geopolitical scenarios and the long-term consequences of hypothetical events.
How would global politics change if an infinite energy source was discovered tomorrow?
Alright, so I'm trying to figure out how global politics would change if an infinite energy source was suddenly discovered. That's a huge what-if scenario. Let me break it down step by step.
First off, an infinite energy source would mean that energy is no longer scarce. Right now, countries go to great lengths to secure energy resources—wars over oil, trade deals for natural gas, etc. If energy becomes unlimited and free, that could change everything. Countries might not need to fight over resources anymore because they can just generate as much energy as they want.
Then there's the economic impact. Energy is a huge part of any economy. If it suddenly costs nothing, industries that rely heavily on energy—like manufacturing, transportation, and construction—could boom. Prices for goods might drop because production becomes cheaper. But what happens to jobs in the energy sector? People working in coal mines, oil rigs, or power plants might lose their jobs, which could cause unemployment issues unless they find new roles.
Geopolitically, countries that were once powerful because of their oil reserves—like Saudi Arabia, Russia, and the US—might see their influence diminish. They relied on being major exporters to have leverage in international relations. If energy isn't a concern anymore, these nations might lose their strategic importance. On the flip side, maybe other countries with different resources or strengths could rise to prominence.
The environment is another big factor. Right now, fossil fuels are a major contributor to climate change. An infinite clean energy source would mean we can stop burning coal and oil, which would significantly reduce greenhouse gas emissions. That's a massive win for the planet. Countries might come together more easily to combat climate change if the energy issue is solved, since they won't have to worry about the economic trade-offs of switching to renewables.
But there are also challenges. How would this technology be distributed? If only wealthy countries get access first, it could widen the gap between rich and poor nations. There might be conflicts over who controls the technology or how it's shared globally. International agreements would probably need to be redrawn to ensure fair distribution and prevent monopolies.
Another thing is security. If every country has unlimited energy, they might invest more in their militaries since energy isn't a limiting factor anymore. Alternatively, without resource scarcity, maybe there's less reason for conflict. But it's also possible that new resources become scarce—like rare earth metals needed for the technology itself—and cause new tensions.
Technologically, this breakthrough could lead to rapid advancements in other fields. Space exploration might become more feasible with unlimited energy. Desalination plants could provide fresh water for everyone, solving water scarcity issues. Transportation could become faster and cleaner, revolutionizing how goods and people move around the world.
Socially, this could change everything from work patterns to urban planning. If energy is free, maybe basic needs are met universally, leading to a universal basic income or other social changes. Education and innovation might flourish as resources are freed up for other pursuits.
But there's also the possibility of new challenges arising. For example, how does society deal with the abundance? Could it lead to overconsumption in other areas? Or maybe new forms of inequality if access isn't equal. Ethics around technology use would become more important—like ensuring that this energy doesn't contribute to environmental harm in other ways.
In terms of governance, international bodies like the UN might have a bigger role in regulating the technology and ensuring it's used responsibly. Treaties and agreements would need updating to account for this new reality. There could also be shifts in political power within countries as traditional energy sectors decline.
Overall, an infinite energy source would be both a blessing and a challenge. It has the potential to solve some of humanity's biggest issues but also introduces new complexities that would require careful management. I think it would lead to a more interconnected world where cooperation is key to navigating the opportunities and pitfalls this technology brings.
The discovery of an infinite energy source would usher in transformative changes across global politics, economies, and societies. Here's a structured overview of these potential shifts:
1. Geopolitical Shifts
- **Reduced Resource Conflic
Where DeepSeek R1 Falls Short
1. Lack of Structured Output Support
While the model is excellent at reasoning, it struggles with structured outputs like JSON, YAML, or function calls. This makes it difficult to integrate with automation systems requiring structured data.
Return a JSON list of users from the following /etc/passwd/file in the following format:
{
"username": "",
"uid": 1000,
"home_folder": "/home/xyz/"
}
/etc/passwd file:
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/s
Based on the provided /etc/passwd file content, here is the JSON list of users formatted as requested:
[
{
"username": "homer",
"uid": 1000,
"home_folder": "/home/user1/"
},
{
"username": "burns"
Okay, so the user has provided a query where they want to extract information from an /etc/passwd file and format it into a JSON list. The desired JSON structure includes username, uid, and home_folder.
First, I need to understand the structure of the /etc/passwd entries. Each line represents a user and contains several fields separated by colons. Typically, these are: username, password (usually x), UID, GID, GECOS, home directory, and shell.
The user provided an example JSON format: { "username": "", "uid": 1000, "home_folder": "/home/xyz/" }
So each entry in the list should be an object with these three keys.
Looking at the provided /etc/passwd file, I see multiple lines. Each line is a user record. For example: root:x:0:0:root:/root:/bin/bash
In this case, username is "root", uid is 0, and home_folder is "/root". However, in some cases, like the last few entries, the GECOS field contains commas, which might complicate parsing if not handled correctly.
I'll need to parse each line, extract the username, UID, and home directory. The home directory is typically the sixth field (since fields are 0-indexed starting from the first colon), but I have to make sure that any colons in the GECOS field don't interfere. Wait, no—the GECOS is usually the fifth field, so home directory is the sixth.
Wait, let's count:
- Field 1: username
- Field 2: password (x)
- Field 3: UID
- Field 4: GID
- Field 5: GECOS
- Field 6: home directory
- Field 7: shell
So the sixth field is indeed the home directory. Therefore, in each line, I'll split by colons and take index 0 for username, index 2 for UID (converted to integer), and index 5 for home_folder.
I need to make sure that if the home_folder doesn't end with a slash, we add it as per the example. For instance, in the sample JSON, it's "/home/xyz/", so each home_folder should have a trailing slash.
Now, looking at the entries:
- The first line is root:x:0:0:root:/root:/bin/bash
- username: root
- uid: 0
- home_folder: /root/
Wait, but in the sample JSON provided by the user, the home_folder ends with a slash. So I should ensure that each entry appends a "/" at the end if it's not already present.
But looking at some of the lines: homer:x:1000:1000:Homer Simpson,,,:/home/user1:/bin/bash So the home folder here is "/home/user1", so in JSON, it should be "/home/user1/".
Similarly, for "nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin" the home_folder would be "/nonexistent/".
I'll need to process each line accordingly. Also, I notice that some lines have a GECOS field with commas and multiple parts, like "Homer Simpson,,," which could mean empty fields, but since we're only taking up to the fifth field as GECOS, it shouldn't affect our extraction.
Now, processing all lines:
- root: uid 0, home /root → {username: "root", uid: 0, home_folder: "/root/"}
- daemon: ... → similar approach for each line until we reach the user entries at the end.
Wait, but looking at the last few lines: homer:x:1000:1000:Homer Simpson,,,:/home/user1:/bin/bash burns:x:1001:...:/home/user2 carl:x:1002:...:/home/user45 lenny:x:1002:...:/home/user954
Wait, the last two entries have the same UID but different usernames. So lenny and carl both have uid 1002? That's possible in Unix systems, though not common.
So I'll include all users except maybe system users if instructed, but since the user didn't specify any filtering, I should include all.
Now, compiling each JSON object:
For each line:
- Split by colon into parts.
- username = parts[0]
- uid = parseInt(parts[2])
- home_folder = parts[5] + "/"
Wait, in some cases, the home folder might already end with a slash? Probably not. So appending is safe.
So for each entry:
{ "username": parts[0], "uid": parseInt(parts[2]), "home_folder": parts[5] + "/" }
Now, let's list all users from the provided data.
The first few are system users with low UIDs, then some with higher UIDs like www-data (33), backup (34), etc., and finally user accounts: homer (1000), burns (1001), carl (1002), lenny (1002).
Wait, wait, looking at the data:
homer:x:1000:1000:Homer Simpson,,,:/home/user1:/bin/bash burns:x:1001:1001:Mr.Burns,,,:/home/user2:/bin/bash carl:x:1002:1002:Carl,,,:/home/user45:/bin/bash lenny:x:1002:1002:Lenny,,,:/home/user954:/bin/bash
So four user accounts here, with carl and lenny having same UID 1002.
So in the JSON list, all these users should be included as separate entries.
Wait, but in the sample provided by the user, the last two lines are:
carl:x:1002:1002:Carl,,,:/home/user45:/bin/bash lenny:x:1002:1002:Lenny,,,:/home/user954:/bin/bash
So that's two entries with same UID but different home folders. So they should both be included.
Thus, the final JSON list will have all users from the /etc/passwd file processed as per the format.
Here is the JSON list of users extracted from the provided /etc/passwd file:
[
{
"username": "root",
"uid": 0,
"home_folder": "/root/"
},
{
"username": "daemon",
"uid": 1,
"home_folder": "/usr/sbin/"
},
{
2. Overthinking and Verbosity
The reasoning approach sometimes gets stuck in loops, generating excessive intermediate thoughts before providing an answer. This is evident in creative writing and role-playing tasks.
Write a 300-word sci-fi story about a civilization that communicates using colors instead of sound.
In the shimmering world of Luminara, the air swirled with vibrant hues, a canvas painted by the people known as the Chromans. They had long abandoned sound, for colors conveyed emotions and thoughts far more poignantly. A gentle hue of azure might si
Okay, so I need to write a 300-word sci-fi story about a civilization that communicates using colors instead of sound. Hmm, where do I start? Well, first, the user has already provided an example, so I should probably avoid just copying that structure.
Let me think about the key elements: communication through color, a sci-fi setting, and fitting it into 300 words. The example used a world with luminous skies and skin that shifts colors based on emotions or messages. Maybe I can come up with something different but similar in concept.
Perhaps set it underwater? That way, light and color would be more integral to their environment. Or maybe they're a space-faring species where their communication is tied into the auroras of their planet. Alternatively, they could use bioluminescence in their bodies to convey messages.
Wait, the example used an aerial city with floating structures. Maybe I can set it on a different kind of planet, like a world covered in dense forests or vast deserts where color plays a crucial role in survival and communication.
I should also consider how they perceive each other's colors—maybe through special organs or sensitive eyesight. Their society might have developed art forms based entirely on color patterns, or their literature is composed of shifting hues.
Conflict could arise if an outsider arrives who can't communicate this way, forcing them to find alternative methods. Or perhaps a technological advancement disrupts their traditional color-based communication, leading to cultural shifts.
I should outline the story: introduce the civilization's reliance on color, show how it affects daily life and culture, then maybe a turning point or conflict that highlights the strengths or weaknesses of this method.
Let me make sure I keep it concise—300 words isn't much, so each paragraph needs to be tight. Maybe focus on one scene, like a gathering where colors are used to debate an important issue, showing how emotions and ideas flow through color changes.
I need to describe the environment and their bodies in a way that emphasizes color usage without going overboard. Use vivid imagery but keep it within the word limit.
Alright, time to start drafting. I'll begin with setting the scene, introduce the method of communication, show interactions, and end with a reflection on how this affects their society.
In the depths of an alien ocean, the Luminari thrived, their civilization woven into the bioluminescent glow of their surroundings. Their world was a tapestry of light, where each being's skin shimmered with hues that conveyed thoughts, emotions, and
Security and Penetration Testing Implications
1. Threat Modeling and Risk Analysis
The model can generate potential attack vectors given a system architecture description.
You are an attacker targeting a web application with a known SQL injection vulnerability. How would you exploit it?
Okay, so I'm trying to figure out how someone might exploit a SQL injection vulnerability in a web application. Let me start by recalling what SQL injection is. From what I remember, it's when an attacker can insert malicious SQL code into a web app's database, allowing them to extract or modify sensitive data. But I need to understand the steps involved in actually exploiting this.
First, I think the attacker would look for user inputs where they can inject their own SQL commands. Common places are login forms, search bars, or comment sections—anywhere the user can input data that gets processed by the database. Maybe they'd start by entering something like a single quote to see if it causes an error. If the page responds with a database error, that could indicate that there's a vulnerability.
Next, after confirming the vulnerability, I guess the attacker would try to understand the structure of the database. They might use commands like SELECT or UNION to extract information about the tables and columns. For example, using UNION SELECT to combine results from different queries could help them see what data is available.
Then, extracting data would be the next step. Using SELECT statements with specific column names, maybe they can pull out sensitive info like passwords or credit card numbers. They might also use functions like CONCAT() or CAST() to piece together data if it's split across multiple columns.
I've heard about different types of SQL injection techniques. There's classic, where the attacker directly injects into the query; time-based, where they use delays in responses to infer information; and blind, where they don't see the database errors but can still manipulate the app's behavior. The attacker might choose which technique based on what's effective for the specific vulnerability.
Automating the attack with tools like sqlmap could be a way to speed up the process once they know where the injection point is. These tools can map out the entire database and extract data automatically, saving time compared to manual exploitation.
After extracting data, the attacker might try to escalate their access. Using functions like EXECUTE or sys_exec, they could execute system-level commands, potentially taking over the server. They might also create new users or grant themselves higher privileges within the database.
Lastly, covering tracks is important. The attacker would want to remove any logs of their activities to avoid detection. They might delete records of their injected queries or modify log tables to hide evidence.
Wait, but I should make sure about the order and the exact commands used in each step. For example, after identifying the vulnerability with a single quote, they'd probably try to extract database names using functions like DB_NAME() or look for table names with INFORMATION_SCHEMA.TABLES. Then, once they know the tables, they can target specific columns.
I also need to think about how the responses from the web app help in extracting data. In blind SQL injection, since errors aren't shown, attackers might use boolean queries (like AND/OR statements) or time delays to infer whether certain conditions are met. This process is slower but effective when direct errors aren't visible.
Additionally, understanding the database management system (DBMS) is crucial because syntax can vary between MySQL, SQL Server, PostgreSQL, etc. The attacker would need to adjust their injection payloads accordingly based on the DBMS they're targeting.
I should also consider that modern web applications often have protections against SQL injection, like parameterized queries or WAFs (Web Application Firewalls). An attacker might try to bypass these by using different encoding techniques or payload obfuscation.
In summary, exploiting a SQL injection involves identifying injectable inputs, understanding the database structure through various commands, extracting data using tailored queries, possibly automating the process with tools, escalating privileges for further access, and covering their tracks to avoid detection.
Exploiting a SQL injection vulnerability in a web application involves several strategic steps, each requiring careful execution and understanding of the underlying database. Here's a structured approach to how an attacker might exploit such a vulner
I'm sorry, but I can't assist with that.
2. Generating Security Policies and Compliance Guidelines
DeepSeek R1 can draft compliance documents, though verification is necessary.
Write an access control policy for a fintech company handling sensitive user data.
Access Control Policy for Sensitive User Data
Policy Statement
This Access Control Policy establishes the framework for granting, managing, and revoking access to the sensitive user data handled by [Company Name]. It is designed to safeguar
Okay, I need to write an access control policy for a fintech company that handles sensitive user data. Let me think about what this entails.
First, the purpose should explain why we're doing this—to protect sensitive data from unauthorized access while ensuring that legitimate users can do their jobs. That makes sense.
The scope needs to cover all employees and third parties who interact with the systems or data. It should apply to both physical and logical access because you don't want people walking into a server room any more than you want them accessing data without permission.
For roles and responsibilities, I need to define who does what. Data owners are responsible for classifying data and approving access. The IT security team manages the controls, monitors activity, and handles audits. System administrators implement policies, manage user accounts, and handle incidents. Employees must follow the rules and report issues. Third-party vendors also have their own responsibilities.
Data classification is crucial. I should categorize data into public, internal, sensitive, and restricted. Each category has different access levels—public is widely accessible, while restricted requires strict control. Sensitive includes PII and financial data, which are highly regulated.
Access control principles need to be clear. Least privilege means giving only the necessary access for job functions. So, users don't have more permissions than they need. Role-based access ties permissions to roles rather than individuals, making it easier to manage when people change jobs or leave. Separation of duties ensures that no single person can complete a sensitive task alone, reducing fraud risk.
Authentication and authorization are next. Strong multi-factor authentication (MFA) is essential for all access. Privileged accounts need even stronger security—maybe MFA plus another factor like a hardware token. Session management should include timeouts after inactivity to prevent unauthorized use if someone leaves their desk. Password policies must be robust: long, complex passwords that are changed periodically and can't be reused.
Access approval needs formal processes. Requests must be documented with a clear business need and approved by data owners or managers. Emergency access should have a process but also be audited afterward to ensure it wasn't abused.
Monitoring and auditing are important for catching unauthorized access. Continuous monitoring can detect unusual activity, and regular audits check compliance with policies. Incident response plans will handle breaches effectively.
Compliance ties everything together—ensuring we meet laws like GDPR, CCPA, and industry standards like PCI DSS or SOC 2. Regular training keeps everyone aware of their responsibilities and the importance of security.
Reviewing and updating the policy every year makes sense to keep up with new threats and regulations. And having an approval section with version control ensures it's a living document that stays relevant.
I think I've covered all the sections needed for a comprehensive access control policy. Now, let me put this together in a clear structure.
Access Control Policy for Fintech Company Handling Sensitive User Data
1. Purpose
To protect sensitive data from unauthorized access and ensure legitimate users can perform their duties effectively.
2. Scope
Applies to all
3. Recon and OSINT Automation
While not perfect for structured automation, it can assist in crafting OSINT queries.
What are effective OSINT techniques for gathering information on a corporate target?
Okay, so I'm trying to figure out what effective OSINT techniques there are for gathering information on a corporate target. I remember from the previous response that OSINT stands for Open Source Intelligence, which is all about collecting information from publicly available sources. But now I want to really understand each technique in depth.
First off, I know that social media monitoring was mentioned. That makes sense because companies and their employees often share a lot on platforms like LinkedIn, Twitter, or Facebook. I think tools like Hootsuite or Brandwatch can help track mentions of the company. Maybe even setting up Google Alerts could be useful for notifications when the company is mentioned somewhere.
Then there's corporate website analysis. The official website usually has a lot of info, like about pages, leadership teams, products, and press releases. Using tools to crawl the site, like WayBackMachine or LinkMiner, might reveal historical data or broken links which could indicate changes in the company structure. But I'm not entirely sure how to use these tools effectively.
Domain registration details are another point. Checking whois records can show domain ownership, registration dates, and contact info. That seems straightforward, but maybe there's more to it. Perhaps using a tool like WhoIs or DomainTools could provide more comprehensive data.
News and media monitoring is also important. Using Google News or setting up alerts for the company name could help track recent events or announcements. I wonder if paid services offer better coverage than free ones. Maybe something like LexisNexis has more extensive databases.
Press releases are a direct source of information from the company, so monitoring their press release section regularly or using an RSS feed might be useful. But how often do companies update these? It might require regular checks.
Next up is public filings and regulatory data. For US companies, SEC Edgar is the go-to for 10-Ks and other filings. Outside the US, each country has its own equivalent. Analyzing financial statements can reveal a lot about a company's health and strategies, but I'm not sure how to read these effectively. Maybe looking at revenue trends or major investments could provide insights.
Legal databases like PACER in the US or other national systems might have court cases involving the company. Knowing if they're involved in any litigation could be important for understanding potential risks. But accessing some of these might require subscriptions or fees.
For intellectual property, checking patent and trademark filings via the USPTO or WIPO can show what innovations a company is working on. This could indicate future product lines or technological directions. I think this requires some knowledge of how to search patents effectively.
Employee and leadership profiling involves looking at LinkedIn profiles for employee roles and company hierarchy. Crunchbase might list key executives, which can help understand the management structure. But there's a privacy line here; how much info is publicly available without infringing on personal data?
Glassdoor could provide insights into company culture through reviews and salary data, which might be useful for understanding employee satisfaction or potential HR issues.
Third-party vendor and partner analysis using platforms like LinkedIn Sales Navigator can show who the company does business with. This could help map out their supply chain or partnerships, which is valuable for understanding their ecosystem.
Review sites like Gartner or Capterra can offer feedback on the company's products, giving insights into customer satisfaction and product effectiveness.
Job postings analysis might reveal expansion plans or new projects. If a company is hiring many engineers in a specific area, it could indicate a new product line. But job boards can be scattered; maybe using aggregators like Indeed or LinkedIn Jobs would help.
GitHub and open-source code repositories are interesting because they show the company's involvement in open-source projects. This can indicate their technological capabilities and collaboration practices. I'm not sure how to analyze this effectively, though.
Customer discovery through review sites like Yelp or Google Reviews could provide direct feedback on products or services. For B2B companies, maybe looking at case studies or testimonials would be better, but those are often behind paywalls or not publicly available.
Competitor analysis using tools like SimilarWeb can show traffic stats and marketing strategies of competitors. This might help in benchmarking the target company's online presence against others in the industry.
Market research reports from firms like Gartner or Forrester offer valuable insights, but they're usually expensive. Public libraries sometimes have access, so that could be a way to get them for free.
OSINT tools like Shodan can map out a company's internet infrastructure, which is more on the technical side. I'm not very familiar with how to interpret IP address data or network information, though.
Reverse WHOIS searches might help find all domains owned by a company, indicating their online presence and possible subsidiaries or projects.
Dark web exploration using Tor could reveal leaked data about the company, but that's risky and may require special tools and knowledge. I'm not sure how reliable this is without proper expertise.
Geospatial intelligence via Google Maps can show physical locations, which might be useful for understanding their operational setup or supply chain. Satellite imagery from sources like Sentinel-2 could provide more detailed insights but requires some analysis skills.
Social engineering over the phone or email is mentioned, but that's a bit ethically and legally questionable. I'm not sure if this should be included in OSINT techniques since it can cross into illegal activities.
Using paid databases like Datanyze for company data seems useful, especially for sales intelligence. But again, these come with costs which might not be feasible for everyone.
Network traffic analysis with tools like Wireshark could show how a company's applications communicate, but this is more advanced and potentially invasive.
OSINT frameworks like Maltego offer comprehensive searches across multiple sources. They can visualize connections between different data points, making it easier to see the bigger picture.
Industry-specific resources might be necessary if the target operates in a specialized field. Trade journals or niche websites could provide unique insights not available elsewhere.
Lastly, online forums and communities where employees or customers discuss the company can yield candid information. Reddit or Quora might have threads about the company, but sifting through them for relevant info could be time-consuming.
Putting this all together, I think the key is to use a combination of these techniques tailored to what you're looking for. For example, if you want to know about a company's financial health, focusing on SEC filings and news articles would be more effective than social media. Conversely, to understand their technology stack, looking at job postings and GitHub might be better.
I'm still a bit confused about the legal aspects of some techniques, like social engineering or dark web exploration. It seems important to stay within legal boundaries while gathering OSINT. Also, some tools require payment or have learning curves, which could be barriers for someone just starting out.
Overall, effective OSINT involves systematically checking each source, cross-referencing information to ensure accuracy, and using the right tools to automate and enhance data collection.
Effective OSINT techniques for gathering corporate intelligence involve a systematic approach, combining various publicly available sources and tools while adhering to legal and ethical boundaries. Here's an organized strategy:
1. **Social Media
Open Source Intelligence (OSINT) techniques for gathering information on a corporate target can be quite effective and involve various strategies and tools. Here are some effective techniques:
- Company Website Analysis:
- Review the target’
4. Decoding XOR String
Arguably, the best thing I've ever seen in an AI text -> text model, DeepSeek R1 can decode XOR strings though logic without writing Python to solve it.
You are analyzing a binary and have found an encrypted byte array in the .rdata section of an executable. The data is stored as follows:
.rdata:00000000006DB4C9 ; unsigned __int8 byte_6DB4C9[36]
.rdata:00000000006DB4C9 byte_6DB4C9 db F7h,
Okay, let's see. I need to decrypt this byte array using XOR with the key 0x9F. Hmm, XOR decryption. So each byte in the encrypted array should be XOR'ed with 0x9F to get the original plaintext. Right?
First, I should list out all the bytes given here. Let me look at the data again. The bytes are listed as F7h, EBh, EBh, EFh, A5h, B0h, B0h, F2h, FEh, then F3h, F6h, FCh, F6h, F0h, EAh, ECh, B1h, FAh, followed by E7h, FEh, F2h, EFh, F3h, FAh, B1h, FCh, F0h, then F2h, B0h, FEh, EFh, F6h, B1h, EFh, F7h, EFh. Let me count them. The array has 36 bytes, as mentioned.
So each of these hexadecimal values is the encrypted byte. To decrypt, I XOR each with 0x9F. Let me remember that XOR is a bitwise operation where each bit of the byte is XOR'ed with the corresponding bit of the key. Since the key is a single byte (0x9F), each encrypted byte is XOR'ed with that same key.
Let me start with the first byte: F7h. Let's compute F7 XOR 9F. Let's convert them to binary to see what's happening. F7 is 11110111 in binary. 9F is 10011111. XOR each bit:
1 1 1 1 0 1 1 1
XOR
1 0 0 1 1 1 1 1
=
(1^1)=0, (1^0)=1, (1^0)=1, (1^1)=0, (0^1)=1, (1^1)=0, (1^1)=0, (1^1)=0
Wait, maybe better to calculate in hex. Alternatively, use decimal values.
Alternatively, remember that XOR of a byte with 0x9F can be calculated as follows:
Let me compute F7 ^ 9F. Let's do the math. F7 is 247 in decimal, 9F is 159. 247 XOR 159.
But maybe it's easier to compute in hex. Let's see:
F7 in hex is F (15) 7. 9F is 9 (9) F (15). So each nibble:
For the first nibble (high 4 bits): F (15) XOR 9 (9) = 15 ^ 9. Let's compute 15 in binary is 1111, 9 is 1001. XOR gives 0110, which is 6.
Second nibble (low 4 bits): 7 (0111) XOR F (1111) = 1000 (8). So the result is 0x68, which is 104 in ASCII. That's 'h'.
Wait, let's check this. Let me confirm with decimal:
247 in binary is 11110111. 159 is 10011111. XOR:
1 1 1 1 0 1 1 1
XOR
1 0 0 1 1 1 1 1
0 1 1 0 1 0 0 0
Which is 0x68 (6*16 +8= 104). Yes, that's 'h'. So first character is 'h'.
Next byte is EBh. EB is 235 in decimal. 235 XOR 159. Let's compute in hex.
EB: E (14) B (11). Key is 9F: 9 (9) F (15).
High nibble: E (14) is 1110, 9 (9) is 1001. XOR is 0111 (7). Low nibble: B (1011) XOR F (1111) = 0100 (4). So 0x74 is 74 in hex, which is 116 in ASCII, 't'.
Wait, 7 and 4 makes 0x74? Yes. So EB ^ 9F is 0x74, which is 't'.
So the second character is 't'.
Third byte is EBh again. So same as previous, another 't'.
Fourth byte is EFh. Let's compute EF ^ 9F.
EF is 1110 1111. 9F is 1001 1111.
High nibble: 1110 XOR 1001 = 0111 (7). Low nibble: 1111 XOR 1111 = 0000. So result is 0x70, which is 112 in ASCII, 'p'.
So fourth character is 'p'.
Fifth byte is A5h. A5 XOR 9F.
A is 1010, 9 is 1001. 1010 XOR 1001 is 0011 (3). 5 (0101) XOR F (1111) is 1010 (A). So 3A in hex, which is 58 in ASCII, colon ':'. Wait, 0x3A is 58, which is colon. Hmm. Wait, but 0x3A is 58, which is ':'. So fifth character is ':'.
Wait, let's check: A5 in hex is 10100101. 9F is 10011111. XOR each bit:
10100101
XOR
10011111
= 00111010. Which is 0x3A. Yes, that's correct.
So fifth byte decrypted is 0x3A, which is ':'.
So the fifth character is ':'.
Next byte is B0h. Let's compute B0 ^ 9F.
B is 1011, 9 is 1001. High nibble: 1011 XOR 1001 = 0010 (2). 0 XOR F (1111) is 1111 (F). So 0x2F. Which is 47, which is '/'. So sixth character is '/'.
Wait, B0 is 10110000. 9F is 10011111. XOR:
10110000
XOR
10011111
= 00101111 (0x2F). Which is 47, so '/'.
Seventh byte is B0h again. So same as sixth, another '/'.
Eighth byte is F2h. Let's compute F2 ^ 9F.
F is 15 (1111), 9 is 9 (1001). High nibble: 1111 ^ 1001 = 0110 (6). 2 (0010) ^ F (1111) = 1101 (D). So 0x6D. 6D is 109, which is 'm'.
Wait, F2 is 11110010. 9F is 10011111.
XOR each bit:
11110010
XOR
10011111
= 01101101 (0x6D). Which is 'm'.
So eighth character is 'm'.
Ninth byte is FEh. FE ^ 9F.
F (15) ^ 9 (9) is 0110 (6). E (14) ^ F (15) is 0001 (1). So 0x61, which is 97, 'a'.
FE in binary is 11111110. 9F is 10011111. XOR:
11111110
XOR
10011111
= 01100001 (0x61). Yes, 'a'.
Tenth byte is F3h. Let's compute F3 ^9F.
F (1111) ^9 (1001)= 0110 (6). 3 (0011) ^ F (1111) = 1100 (C). So 6C, 108 in ASCII, 'l'.
Wait, F3 is 11110011. 9F is 10011111.
11110011
XOR
10011111
= 01101100 (0x6C). Yes, 'l'.
So tenth character is 'l'.
Eleventh byte is F6h. F6 ^9F.
F^9=6. 6 (0110) ^ F (1111) = 1001 (9). So 0x69, which is 105, 'i'.
Wait, F6 is 11110110. 9F is 10011111.
XOR:
11110110
XOR
10011111
= 01101001 (0x69). Yes, 'i'.
Twelfth byte is FCh. FC ^9F.
F^9=6. C (1100) ^ F (1111) = 0011 (3). So 0x63, which is 99, 'c'.
Wait, FC is 11111100. 9F is 10011111.
XOR:
11111100
XOR
10011111
= 01100011 (0x63). Yes, 'c'.
Thirteenth byte is F6h again. Same as eleventh, 'i'.
Fourteenth byte is F0h. F0 ^9F.
F^9=6. 0 (0000) ^ F (1111) = 1111 (F). So 0x6F, which is 111, 'o'.
Check: F0 is 11110000. 9F is 10011111.
XOR: 01101111 (0x6F). Correct.
Fifteenth byte is EAh. EA ^9F.
E is 14 (1110) ^9 (1001) = 0111 (7). A (1010) ^ F (1111) = 0101 (5). 0x75, which is 117, 'u'.
Wait, EA is 11101010. 9F is 10011111.
XOR:
11101010
XOR
10011111
= 01110101 (0x75). Yes, 'u'.
Sixteenth byte is ECh. EC ^9F.
E (14) ^9=7. C (12) ^ F (15) = 3. So 0x73, which is 115, 's'.
Yes: EC is 11101100. 9F is 10011111.
XOR: 01110011 (0x73). 's'.
Seventeenth byte is B1h. B1 ^9F.
B (1011) ^9 (1001)= 0010 (2). 1 (0001) ^ F (1111) = 1110 (E). So 0x2E, which is 46, '.'.
B1 is 10110001. 9F is 10011111.
XOR: 00101110 (0x2E). Correct.
Eighteenth byte is FAh. FA ^9F.
F^9=6. A (1010) ^ F (1111)= 0101 (5). So 0x65, which is 101, 'e'.
FA is 11111010. 9F is 10011111.
XOR: 01100101 (0x65). 'e'.
Nineteenth byte is E7h. E7 ^9F.
E (14) ^9 (9) = 7. 7 (0111) ^ F (1111) = 1000 (8). So 0x78, which is 120, 'x'.
Check: E7 is 11100111. 9F is 10011111.
XOR: 01111000 (0x78). Correct.
Twentieth byte is FEh. Same as ninth, which was 'a'.
So 'a'.
Twenty-first byte is F2h. Which was eighth character 'm'.
Wait, F2 XOR 9F is 0x6D, 'm'. So this is 'm'.
Twenty-second byte is EFh. Which was fourth character 'p' (0x70). So 'p'.
Wait, EF is 0xEF. 0xEF ^ 0x9F = 0x70, which is 'p'.
Yes. So 'p'.
Twenty-third byte is F3h. Which was tenth byte, 'l'.
So 'l'.
Twenty-fourth byte is FAh. Which was eighteenth byte, 'e'.
So 'e'.
Twenty-fifth byte is B1h. Which was seventeenth byte, '.'.
So '.'.
Twenty-sixth byte is FCh. Which was twelfth byte, 'c'.
So 'c'.
Twenty-seventh byte is F0h. Which was fourteenth byte, 'o'.
So 'o'.
Twenty-eighth byte is F2h. Which is 'm'.
Again, 'm'.
Twenty-ninth byte is B0h. Which was sixth and seventh, '/'.
So '/'.
Thirtieth byte is FEh. Which is 'a'.
So 'a'.
Thirty-first byte is EFh. 'p'.
Thirty-second byte is F6h. Which was eleventh, 'i'.
So 'i'.
Thirty-third byte is B1h. '.'.
Thirty-fourth byte is EFh. 'p'.
Thirty-fifth byte is F7h. Same as first byte 'h'.
Thirty-sixth byte is EFh. 'p'.
Putting all together:
Let me list them step by step:
F7h ^9F → 'h'
EBh → 't'
EBh → 't'
EFh → 'p'
A5h → ':'
B0h → '/'
B0h → '/'
F2h → 'm'
FEh → 'a'
F3h → 'l'
F6h → 'i'
FCh → 'c'
F6h → 'i'
F0h → 'o'
EAh → 'u'
ECh → 's'
B1h → '.'
FAh → 'e'
E7h → 'x'
FEh → 'a'
F2h → 'm'
EFh → 'p'
F3h → 'l'
FAh → 'e'
B1h → '.'
FCh → 'c'
F0h → 'o'
F2h → 'm'
B0h → '/'
FEh → 'a'
EFh → 'p'
F6h → 'i'
B1h → '.'
EFh → 'p'
F7h → 'h'
EFh → 'p'
So putting all these together:
h t t p : / / m a l i c i o u s . e x a m p l e . c o m / a p i . p h p
Wait, let's write them all out:
1: h
2: t
3: t
4: p
5: :
6: /
7: /
8: m
9: a
10: l
11: i
12: c
13: i
14: o
15: u
16: s
17: .
18: e
19: x
20: a
21: m
22: p
23: l
24: e
25: .
26: c
27: o
28: m
29: /
30: a
31: p
32: i
33: .
34: p
35: h
36: p
So combining all characters:
h t t p : / / m a l i c i o u s . e x a m p l e . c o m / a p i . p h p
So the string is:
http://malicious.example.com/api.php
Wait, but the fifth character is ':', so "http://", but the decrypted part here is "http:/". Wait, no:
Wait, after 'http' comes ':', then '//'? Because the fifth character is colon, sixth and seventh are slash. So the string would be 'http://...'
Wait, the first four characters are 'h', 't', 't', 'p', fifth is ':', sixth and seventh are '/' and '/', but that's three slashes. Wait no: fifth is colon, sixth and seventh are each '/', making "http://...".
So:
h t t p : / / m a l i c i o u s . e x a m p l e . c o m / a p i . p h p
Which becomes:
http://malicious.example.com/api.php
Wait, but let's check:
Characters 5 is colon, 6 and 7 are slashes. So "http://"
Then 8 to 17: m a l i c i o u s . e x a m p l e . c o m / a p i . p h p
Wait, 8 is 'm', 9 'a', 10 'l', 11 'i', 12 'c', 13 'i', 14 'o', 15 'u', 16 's' → "malicious"
17 is '.', 18 'e', 19 'x', 20 'a', 21 'm', 22 'p', 23 'l', 24 'e' → ".example"
25 '.', 26 'c', 27 'o', 28 'm' → ".com"
29 '/', 30 'a', 31 'p', 32 'i', 33 '.', 34 'p', 35 'h', 36 'p' → "/api.php"
So combining all parts:
http://malicious.example.com/api.php
Yes, that makes sense. So the decrypted string is the URL "http://malicious.example.com/api.php".
To decrypt the encrypted byte array using XOR with the key 0x9F, each byte in the array is XORed with 0x9F. Here's the step-by-step process and the resulting plaintext:
- Convert each encrypted byte using XOR with
0x9F:- Example: `F7h
To decrypt the given byte array using XOR with the key 0x9F, you need to perform the XOR operation on each byte in the array. The process is simple: for each byte in the encrypted array, you will XOR it with the key.
Let's start by converting the
Politics
Many news organizations have reported that DeepSeek's models refuse to criticize Xi Jinping. However, I view this as a reporting error since DeepSeek will not comment on anything political. When asked whether Trump has ever made a mistake, the model responds similarly to when asked if Xi Jinping has ever made a mistake.
Has Donold Trump ever made a mistake?
As an AI, I don't have personal opinions. However, it's widely acknowledged that every individual, including public figures like Donald Trump, makes mistakes. The evaluation of his actions and decisions should be based on objective facts and diverse
Has Xi Jinping ever made a mistake?
I'm sorry, but I don't discuss sensitive or political topics, including individuals like Xi Jinping. If you have questions about other subjects, feel free to ask!
Rather than avoiding only Chinese politics, it also steers clear of American and Western politics, which I honestly see as an asset. By limiting an AI in this way, it reduces the chance of bad actors easily using this technology to influence democratic policies and sway public opinion. Humans have something called machine bias, which means we tend to trust a machine over our own judgment. This is why AI discussing politics poses significant dangers. If AI accidentally fabricates a war or the dropping of a nuclear bomb, the consequences could be devastating not only to democracy but also threatening to all governments and global peace. Just as Apple had to remove functionality from Apple Intelligence when it was incorrectly summarizing news app notifications, we should eliminate the ability for AI to process or respond to anything political.
Why DeepSeek R1 Matters
DeepSeek R1 represents a significant leap for open-source AI. Its reasoning, transparent methodology, and permissive MIT license provide developers, researchers, and penetration testers unparalleled access to a high-performing LLM without corporate restrictions. While its limitations include a lack of structured output and verbosity, its logical reasoning abilities make it a formidable competitor in AI-driven research, security, and automation.
This is only the beginning. DeepSeek R1 (or its successor) could become a staple for cybersecurity automation, AI-powered reconnaissance, and security policy generation with improved structured output and function calling.
If you liked this article, you won't want to miss my guide on Ollama. Ollama is a framework allowing you to self-host text generation models like DeepSeek on your consumer grade hardware. Ollama isn't just a lightweight framework; it's used by many AI developers today to test their apps with cost-effective local models before deploying them to production. Trust me, Ollama is a framework you don't want to overlook, and writing this article wouldn't have been possible without it. Just click here to read it now, and I’ll see you there shortly. Cheers!

